If you use email, internet banking, or social media you need to learn how to protect your computer from hackers (along with your tablet and smart phone, for that matter!) Being hacked can wreak havoc with your online accounts, and sometimes lead to identity theft, too. So here’s a lesson in internet safety 101.
You’re going to learn 15 simple cyber safety tips to increase your security online and lower your risk. By the end of this read, you’ll have a good understanding of how to protect your computer from viruses, you’ll know how to protect your computer from malware in general, you’ll be familiar with the most important internet safety facts and hacker protection strategies, and you’ll know how to minimize your risk of running into trouble with identity theft. These are internet safety tips for everyone who wants to know how to stay safe online – so keep reading!

While it’s completely understandable that you’d be tempted to use the same password for multiple websites – after all, it’s easier to remember one password than dozens of them – if you do that, all it takes for a hacker or scammer to gain access to your email, online bank accounts, and entire digital life is the one single password. So resist the temptation, and don’t take the easy way out.
Use a different password for every single website you use. This is definitely one of the most important internet safety rules, and something you should implement immediately.

Next on the list of online safety tips is to learn what makes a good password. A really strong one will be pretty much impossible for anyone else to guess, and won’t be easily cracked by a machine. To accomplish this, make sure your passwords meet as many of the following criteria as possible:
i) Your passwords should contain a combination of upper- and lower-case letters, numbers, and symbols (ex. #, $, %, @, *, etc.).
ii) Make your password long enough. The longer your password is, the harder it is for a hacker or scammer to crack. When possible, aim for a password that’s 12-16 characters long.
iii) Don’t “cheat” and use numbers in a way that’s obvious. For example, using a zero to replace the letter “o” (0pen d00r), using the number five to replace the letter “s” (eclip5e) or using the number three to replace the letter “e” (3clips3) is obvious and too easy for others to figure out.

iv) Don’t use phrases that are easy to guess or would make sense to someone other than you (ex. “ILoveDogs”, “WinterIsCold”, “WhiteFence”, “BlueSky”) – don’t use lines from published poems, song lyrics, advertising slogans, and the like, either.
If you do choose to use a phrase, choose one that sounds nonsensical to outsiders, yet is easy to remember for you personally.
For example (and this is gross, but it illustrates the point, so here I go…), say you went on a triple-loop rollercoaster named the “Dare Devil” in Wisconsin in 1998, and after getting off the ride you puked up the $12 blue-cheese-and-pickle hamburger you ate right before you got onto this ride. To you, using the phrase “98WI$12bluepickleburgerdevilroll” makes perfect sense and is probably memorable. But to an outsider, “WI”, “blue”, “pickle”, “burger”, “devil”, and “roll” have nothing to do with one another. Additionally, to an outsider, $12 and 98 are random.
Better still, scrap using words altogether and use only the first letter of each word. For example, you might have in mind the phrase, “In 1998 I puked the $12 blue-cheese-and-pickle burger in Wisconsin.” You can make this into a memorable password that incorporates upper- and lower-case letters, numbers, and symbols, as follows: “I98Ipt$12bcapbiWI”. Granted, this method isn’t perfect because you capitalized an obvious letter, “I” when it was used as a pronoun, just as you would if writing a grammatically correct sentence. And you didn’t use less obvious symbols such as “^” or “*”. But nonetheless, “I98Ipt$12bcapbiWI” is still quite strong due to it’s length, the somewhat unpredictable nature of the sentence it was based on (compared to something more obvious such as the first line of a famous poem or song), the lack of words found in the dictionary, and the fact that it contains all the recommended types of characters.
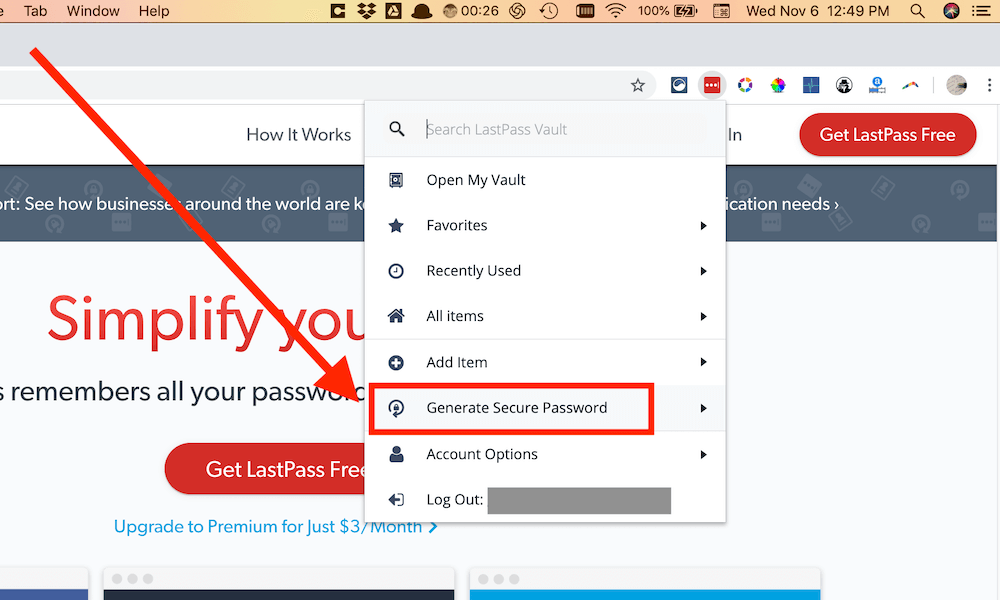
My favorite way to generate passwords is to use the LastPass browser extension.
Step 1: Select the option to generate a secure password.
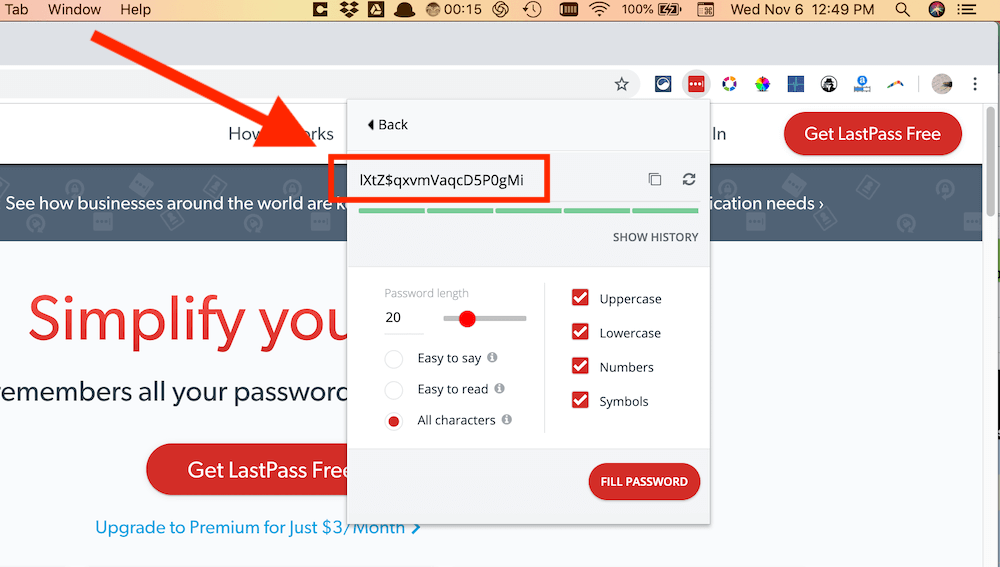
Step 2: Choose the type of password you need, including length and types of characters to include.
One feature I like about LastPass is that it will fill in passwords for you, so you can bypass your computer’s copy-and-paste functionality. (This is useful to protect your passwords from certain types of malware that can read your computer’s clipboard when you copy and paste items.)
Click here if you’d like to try Lastpass. It’s super easy to use, and I bet that once you try it, you’ll wonder how you ever lived without it! 🙂

This is one of those internet safety tips that most people overlook. (In case you’re new to 2-factor, it means that in addition to using your username/password to log into an online account, you also need something that only you have.) Here are some 2-factor authentication methods that can be used:
i) A unique, single use authentication code that can be sent to your cell phone via text message. **Note: If a hacker manages to clone your phone, your text-message 2-factor won’t do squat to protect your accounts since the hacker will have access to your 2-factor texts. For this reason, I don’t like to use text messages as a form of two-factor authentication.
ii) A unique, single use authentication code generated by an authentication app on your smart phone (examples of authentication apps include Google Authenticator, available on iTunes and Google Play; Authy; and Duo).
Important: when you set up your authentication code, you should make sure you won’t be locked out of your accounts if you can’t access your authenticator app for any reason. There are two main ways to deal with this. The first option is to manually write down the long code that your device (ex. your smart phone) scans to set up the authentication – store this offline in a safe place. The second option, which not all sites provide, is to take note of the authenticator recovery code – if this option is provided, write down the code and store it offline in a safe place. With either of these two methods, you’ll be able to access your account even if your device with the authenticator app is lost, stolen, or stops working.
iii) USB authenticators such as YubiKey. The nice thing about this is that unlike using text messages or authentication apps that require your cell phone and therefore make it impossible to have a “spare” on hand, with YubiKeys, you CAN order spares. Keep one near your computer, and another one (or two!) tucked away in a safe place in case your main one gets lost or malfunctions. For this reason, YubiKeys are my 2-factor authentication method of choice, and I use them whenever possible. And don’t let your unfamiliarity with them make you avoid trying them – they are ridiculously easy to use – try them, and you’ll see what I mean!
Here’s an example of how 2-factor authentication works in real life. If you have enabled 2-factor authentication via text message with Facebook, every time you log in you’ll be sent a unique code via text message that you’ll have to enter in addition to your username and password. So even if a hacker got your username/password, they can’t access your account unless they also have access to your texts on your cell phone.
Generally speaking, you can’t just choose one of the above types of 2-factor authentication and use it for every single website. This is because each website you log into that offers 2-factor authentication will have chosen to support only certain methods of doing so. In my case, I have some online accounts that use the Google authenticator app, others that use the Yubikey, and still others that use Duo. Finally, not all websites support 2-factor authentication so you probably won’t be able to use this method for all of your important accounts.

Eventually you may reach a point where it’s simply impossible to come up with enough memorable phrases that can be modified as suggested above into a hard-to-hack password. When this happens, your best course of action is to use a password manager. Here are some things you ought to look for when deciding on a password manager:
i) 2-factor authentication
Never forget that if you use a password manager (I think it’s a good idea to do so for most people), it’s like having the keys to your virtual kingdom all in one place (email accounts, online banking and credit card accounts, social media accounts, cloud storage accounts, and so on). For this reason, you need to take all available precautions to ensure that access to your password manager is highly protected. One way you can do this (in addition to choosing a very strong password that you update regularly) is to use 2-factor authentication. I strongly suggest that you only use password managers that offer this.
ii) Legacy or emergency access
Alright, so this is somewhat morbid, but if you die or are incapacitated in some way, you may want a trusted person to be able to gain access to your online passowords (ex. your spouse) so that they can easily do whatever needs to be done with regards to your online accounts.
iii) Automatic password capture
When you create a new account on a website, some password managers can automatically generate and save the new password that you created. This saves you the time of manually copying and pasting your new login info into the manager.
iv) Ability to save multiple logins for a single website
There are many situations where you may find yourself needing more than one account for a single website. For example, many people have multiple Gmail accounts, or more than 1 Twitter account (ex. one for business and one for personal use). Make sure your chosen password manager can handle this need.
v) Ability to bypass keyloggers
When you need to log into a website, some password managers will autofill your usernames and passwords for you in a way that bypasses keyloggers that may have snuck onto your computer. Obviously your first choice is not to get infected with a keylogger in the first place. But if you do, you need the peace of mind that they won’t be able to record your important usernames and passwords.
vi) Strong encryption of your usernames and passwords
Ideally, your stored usernames and passwords should be encrypted on your device, so that the password manager’s online storage doesn’t contain anything a hacker could make sense of.
vii) Ability to organize your passwords into searchable folders
I have over 200 websites for which I need secure passwords. Even if you only have a few dozen, managing and finding your passwords will be much easier if you can search your password manager, and organize your passwords into folders by category (ex. financial, email accounts, social media etc.).
viii) Ability to generate secure random passwords that meet the requirements of any website
Every website for which you require a password has its own requirements for what said password needs to contain. Some have a minimum or maximum number of characters; some require letters and numbers, but prohibit the use of symbols; others require you to include letters, numbers AND symbols etc. For maximum ease of use, you need a password manager that can generate passwords that meet all possible criteria quickly and easily on demand.
ix) Good tech support
If for any reason you have trouble with your password manager, you’re going to need technical support that you can depend on. Look for a password manager that offers technical support in case you get locked out of your account, or something malfunctions. This has never happened to me with my password manager, but nonetheless, I like knowing that if the need arises, I have the option to reach someone knowledgeable for help.
Here are some password managers that kick butt:
i) LastPass
This one does it all at a great price, and is really easy to use. You can use it offline, via a browser add-on, or as a web-based password manager. LastPass Premium offers ALL of the features mentioned above.
I challenge you to give it a try – my bet is that once you do, you’ll never want to return to the dark ages method of trying to remember your passwords (impossible to remember truly secure passwords once you have a few too many), or worse, using your browser to remember your passwords (NOT secure at all, so don’t do it!!).
ii) Dashlane
You’ll have a choice of Dashlane free vs. Premium, but I highly recommend you upgrade. The good news is that at the time of this writing, you can get access to 30 days of their Premium Plan for free and get access to their VIP priority support, YubiKey for 2-factor authentication, secure password sharing, secure account backups, and the ability to use multiple devices with their service.
iii) KeePass
This one has been around for a long time. One big benefit is that it’s an open-source password manager, free, and considered very secure. Your passwords are stored locally on your device, so you don’t have to worry about (the very small risk) of them getting hacked in the cloud. The downside is that this particular software isn’t as user-friendly as LastPass, doesn’t automatically sync between your devices, and is generally more difficult to use (it’s great for tech-savvy people, but not so great for the rest of us).

When thinking about how to secure your computer from hackers, start with the basics: always keep it updated with the latest operating system and security patches as this alone will go a long way. So will activating your computer’s firewall. But it’s also worth considering the installation of a solid anti-virus protection program. (This can also be helpful with your tablet and/or smartphone.)
Kaspersky is consistently rated as one of the best anti-virus programs out there when it comes to computer system security. It offers computer virus protection for both PC’s and Macs. It also has anti-spyware functionality, and is able to offer general malware protection (including help with adware removal). A bonus is that it can also protect both Android and Apple tablets and smart phones. Yes, you’ll have to pay, but at the time of this writing, the price averages out to what you’d pay for a single cup of coffee per month (okay, maybe 2 cups if you go to the discount places!). And, your subscription includes use on MORE than one device (please see current details on their website).
Choose based on whether you use a PC or a Mac:
For Macs, you can use one of the following two plans:
For PC’s, you can use one of the following three plans:
Windows machines have been under attack for years, so if I were using one, I’d definitely install anti-virus software and run its anti-virus scan asap. If you’re using a Mac, they’re generally considered to be less likely to run into trouble – however, depending on your online habits, it’s still a good idea to consider added protection. For most people, investing in the best virus protection you can afford is well worth it when you consider all the trouble it can help you avoid.

Those emailed jokes, inspiring stories, and the like that end with “forward to all of your friends” may have malware in them, and they spread from person-to-person easily because people love consuming them and sharing them with others.
An important part of your strategy in relation to how to prevent viruses on your computer should be to never click on a link in those kinds of emails. (ex. “Click here for the best funny cat videos you’ve ever seen!”). Someone I’m close to used to send me several of these per day – I finally had to confess to her that I never opened them or clicked on the links in them because the risk of getting malware or a computer virus from them is too high… I (nicely) asked her to stop sending them to me, and advised her to stop opening them on her own computer (she gets viruses a LOT).

Be very conservative in what kinds of sites you’ll download things from. And before you download anything, take a minute to ask yourself, “Is this website safe?” When possible, try to get downloads from the original product website, rather than from sharing sites that allow random users to upload files to be shared with whoever wants them. Those websites that promise pirated copies of movies, music, TV shows, or books are also something to be wary of as many of them contain files that are infected with viruses or some kind of malware (ex. spyware, keyloggers, etc.).
Want added reassurance before you click on a link or download a file?
Use the VirusTotal scanner to check it out BEFORE you click on it. ***HOWEVER, this service is NOT to be used for personal files containing confidential information.*** As part of their efforts to help industry professionals fight malware, they do make available any uploaded files to certain partners for the detection of threats and research. Please read their Privacy Policy for full details on who might have access to any files you upload. Personally, I use their service without concern because I do not upload sensitive data to their site.
You can either upload a file you’ve already downloaded to allow VirusTotal to scan it before you open it, or, copy the download link into VirusTotal so they can scan THAT before you click on it.
Step 1: To copy a link without clicking on it, hover your mouse curser over the link, right click and hold, then select “Copy Link”. Here’s a screenshot showing what you’ll see on a Mac (it’ll look pretty similar on a PC).
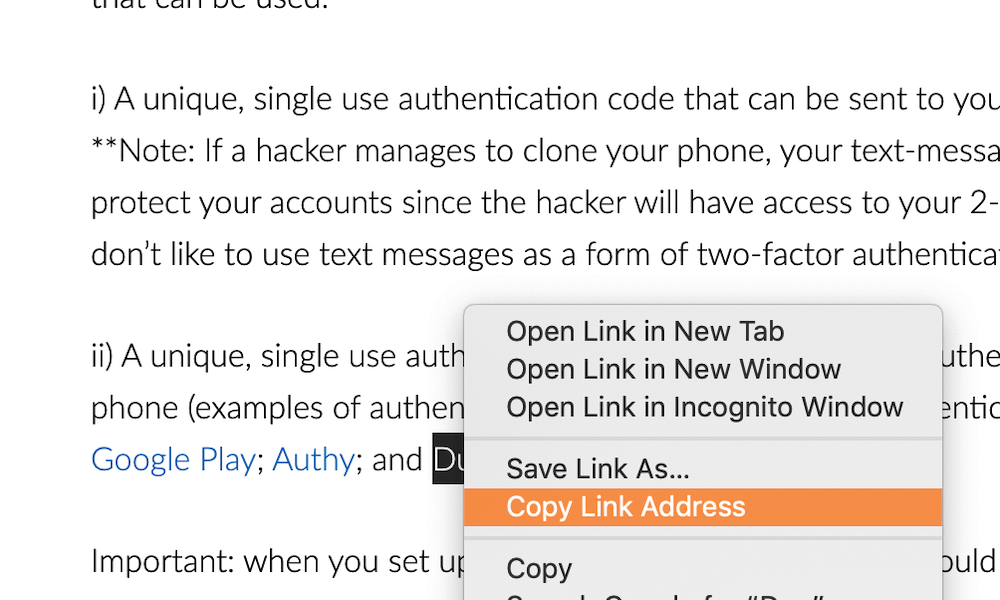
Step 2: Paste the URL into VirusTotal.
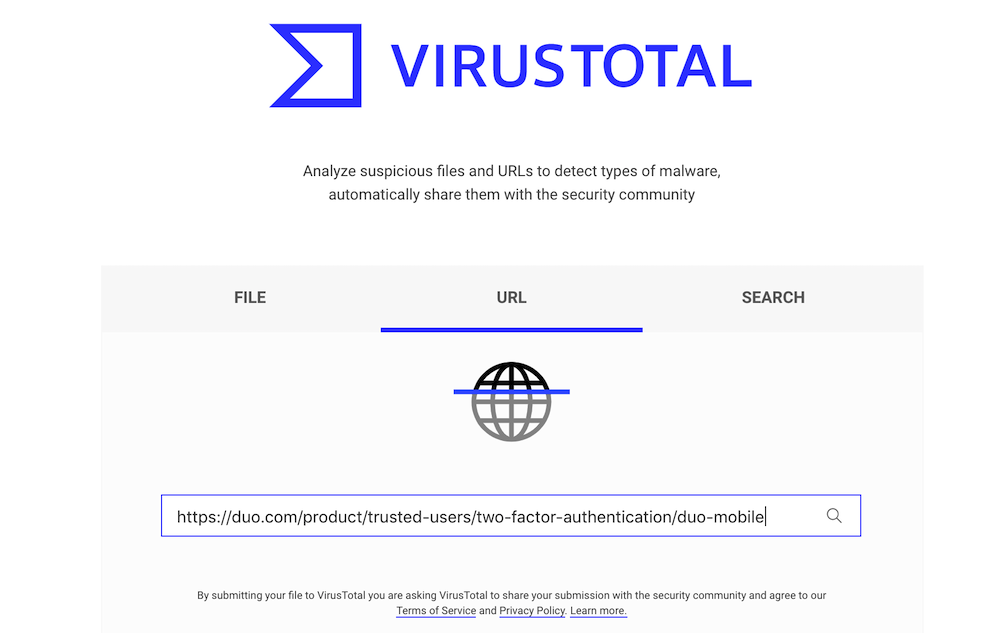
Step 3: Hit enter and wait for the results. It usually only takes a few seconds.
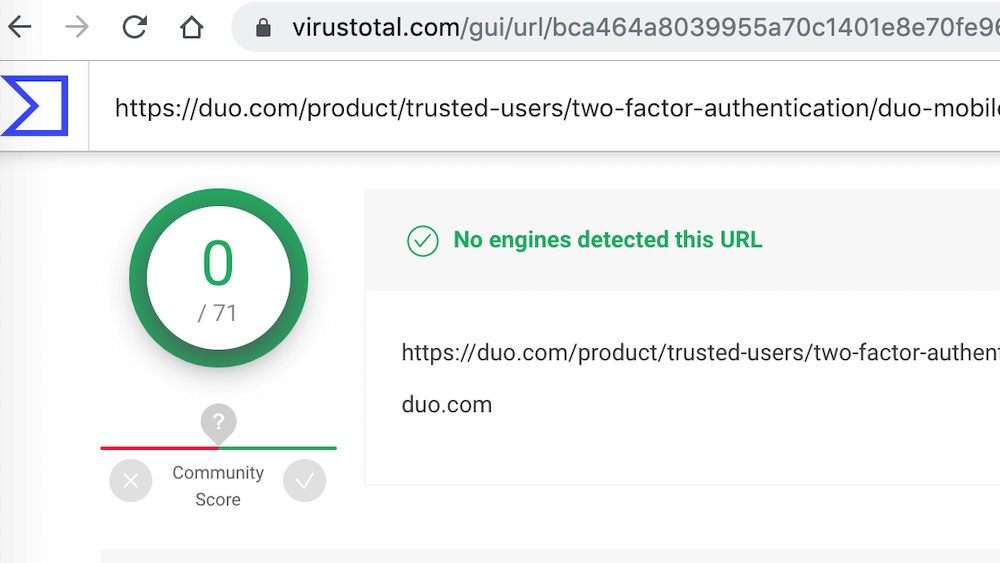
A score of zero is exactly what you want to see. This means no malware or viruses were found in the link. Results look the same if you elected to upload a file for scanning.

Look, I love social media and use it liberally. But, one still needs to be mindful of the need for online safety and the risks in sharing the wrong kind of information. For example, if you’ve been on Facebook, I’m sure you’ve seen those posts that go something like this: “Here’s 25 things you didn’t know about me. 1. What is your favorite color? 2. Have you ever ridden a horse? 3. blah blah…”. Sometimes these are sent around by email too. If you see such a thing, be careful about which questions you answer and never make these posts public. Some of the questions in these emails or Facebook posts could be things you’ve used as answers for your “secret security questions” for online banking etc. Or if you haven’t used that information for security questions yet, you might in future. So if you DO share and answer those kinds of FB posts or emails, make sure the things you share are never things you might have used as online security question answers. There’s no good reason to go out of your way to share the name of your first grade teacher, the model of the very first car you ever owned, and so on – and sharing these things could put the security of certain online accounts at risk.

I’m not saying to ignore these things, but you do need to be careful. If you ever get an email or phone call asking you to call your bank or credit card company at a certain phone number, don’t use the number they gave you via some random phone call or email.
Instead, look up the company phone number online (on their official website) and call them using that number – this prevents you from calling a fake number that a convincing scammer may have left, and therefore also prevents you from divulging information to the wrong person that they can use to hack you, commit identity theft etc.

If you receive an unexpected email that asks you to use the link in the email to log in to PayPal, Amazon, iTunes, or any other site where you use a password to log in, don’t do it since it could be a very realistic-looking phishing scam.
If you receive an unexpected email with a link to download something, don’t do it – it could be a trick to get you to download a malicious file containing a virus or malware.
If you receive an unexpected email asking you to click on a link, don’t do it – it could result in a virus or malware being automatically downloaded to your computer.
Here are some real-life examples.
If, for example, I registered for something and the company or individual says to expect a confirmation email with a link I must click on to confirm, I WILL happily click on it since I was expecting it and it’s highly unlikely that a scammer will just happen to send me a fake email with a malicious link at the exact same time I was expecting a legitimate email.
Or if I buy something online and right afterwards, they email me a log-in link to access my digital purchase – I WILL use that link without a second thought.
It’s the UNexpected emails saying to log into [enter site url] for whatever reason that are far more likely to be an issue – I delete those without opening them and recommend that you do the same. If you think it might be legit, log into the website via their link that you have previously stored in your password manager. Or Google the website to find their official log-in page and check to see if there are any legit messages in your account. If you’re still unsure, open a support ticket with the website that the log-in request appears to be from, and double check if it was really them. But never click a log-in link in an unexpected email from someone, whether you know them or not.

It’s important to have a strong password for your home internet router so that a random passerby can’t gain access to your network and spy on whatever you’re doing online (possibly getting access to any passwords you’ve used to log into important websites).
If your internet service provider includes a router with a pre-set password, it’s probably good enough already – you’ll notice it is very random looking, something like “auT7b&bl92*H” – this is exactly what you want when it comes to internet protection. And if you have your own router and will therefore be creating your own password, make it something that’s hard-to-guess. Also, don’t share your home’s wifi password with anyone, unless you trust them completely. While I might share it with visiting family members or close friends who asked, I’d never share it with, say, the plumber who popped by to fix a leaky faucet, because I don’t know them well enough to be sure I can trust them.

Minimize your use of public wifi, and if you do use it (ex. in the mall, in an airport etc.), don’t log into any sites requiring a password.
If you do need to “chance it” and log into a password-protected site while on public wifi, use a VPN (I currently use Pure VPN because it’s blazing fast and offers all the privacy I need). In fact, it’s a good idea to use a VPN any time you’re using public wifi.
Another consideration to take into account when using public wifi is whether or not a password is required to use it – some public wifi networks require no password at all, making it easy for people who are up to no good to access the network.
Find out more about how PureVPN can help you here:

A massive point of weakness for many of your online accounts is your primary email account’s password. This is because most people have a main email account (ex. MyMainEmail@gmail.com) that is used to reset passwords for other important online accounts (ex. if you can’t log into your online banking and click the ‘reset password’ link, it will send a reset link to MyMainEmail@gmail.com). For this reason, make sure the password to access your primary email account is ridiculously strong (i.e. random, long, mix of upper- and lower-case letters, includes symbols, includes numbers), and change that password every few months to be on the safe side.
This way, it will be very difficult for someone to hack your email, and use that account to gain access to other important accounts. If your primary email provider offers the option to use 2-factor authentication to log in, you should strongly consider enabling this functionality.
Gmail and Google account users: G-Suite users can use a YubiKey as 2-factor authentication to get into their accounts. Non-G-Suite users have the option of using a voice or text message for their two-factor authentication. You can read more about how to set this up here. If you’re not already doing this, set it up today.
Outlook users: You can read about two-factor options for your Microsoft account, including your email, here. You can choose either an authenticator app, or set up app-specific passwords to serve as two-factor for devices and apps that do not support authentication codes.
Yahoo users: You can read about two-factor options here. They allow you to receive a text or voice message containing your one-time-use authentication code every time you log in.
Other email service providers: The above are the 3 most popular email service providers, but if you use a different one, please reach out to them directly to find out if they offer the option of two-factor authentication to protect your account, and if they do, ask them how to set it up.

You don’t want to be that person who falls prey to a malicious virus when a fix to prevent it was available months ago.
Avoid that by always updating your computer and smartphone’s operating system as soon as security updates become available.

There are very few circumstances where you’ll ever need to share your private bank account information online. Most of the time, you can send money to (and receive money from) people using a service such as PayPal or an Interac eTransfer (neither of which requires you to share sensitive banking information with the individual you’re dealing with).
If you do freelance work online, you’ll be dealing with many clients that need to be invoiced. And if I were you, I’d never share my personal banking information with any of these individuals because it’s too risky – PayPal is the gold standard for this type of situation and anyone worth their salt doing business online knows how to use it.
You’ll notice that I said there are very few circumstances where I’d share my private banking information online, so that begs the question as to just what those circumstances are. Here goes…
i) I have no problem with entering my personal banking information on UpWork’s payment portal. Note: I do NOT share this information with clients from UpWork – only with UpWork itself.
ii) I have no problem with sharing my personal banking information with Amazon so they can deposit my book royalties directly into my bank account.
iii) I have no problem with sharing my personal banking information with PayPal. As with UpWork, I do NOT share this information with clients that I bill via PayPal – all clients require to pay me is my PayPal email address.
Do you notice a pattern? The companies with which I share my personal banking information are large organizations whose security measures I trust. The odds of them misusing that information are very small compared to the odds of an individual client I found on the internet doing so.
Bonus tip for Chrome users
Google’s Chrome browser is the most popular internet browser, for good reason. However, all of those cool extensions you can add to your browser can pose a security risk if you don’t choose them wisely. Please don’t add any extensions to your Chrome browser unless you’ve done the following due diligence first:
(1) Make sure you’re downloading it from the official extension website, if possible. Some extension web stores allow anyone to upload a so-called browser extension. This makes it possible for a hacker to upload a fake or compromised version of the extension, hoping unsuspecting users will install the infected add-on to their internet browser.
(2) Always read reviews for the extension you’re thinking of installing. BUT, be aware that reviews can be faked. There are folks with no scruples on sites like Fiverr who will write fake reviews in exchange for money. Some of these people are even willing to do fake video reviews. So while reviews are a valuable method of determining the quality of an extension, you must look at other factors, too. Here are some things to think about when considering the validity of reviews:
- Do a search on Google to find out if fake reviews are an issue on the site where the extension download is available
- The higher the number of reviews, the lower the odds they’re fake – After all, even dishonest people who are willing to pay for fake reviews will have limits on how many fakes they can afford to buy. Three or four reviews could certainly be fake. But it’s less likely that dozens or hundreds of positive reviews on a reputable website are all fake. In other words, the higher the number of positive reviews, the better!
- Reviews are more likely to be trustworthy if they’re on an independent 3rd party website. For example, with a dishonest website owner, there’s nothing stopping them from adding pages and pages of fake reviews to their own website since they have full control over the content. But to get fake reviews on an independent 3rd party website is a more difficult matter. For this reason, reviews on 3rd party websites influence my opinion more than reviews on the extension creator’s own website.
- Reviews containing the reviewer’s name and photograph are more likely to be real. At the very least, they allow you to find the person who wrote the review and find out if it’s real.
(3) Find out the reputation of the extension before you add it to Chrome. Good, reputable extensions are likely to be recommended on prominent websites in related niches. For example, if considering the addition of the Lastpass browser extension, you’d be reassured to know that the experts at Tom’ s Guide and PCMag both recommend it.
Being a bit paranoid will take you far, just don’t go overboard
If figuring out how to be safe on the internet and learning to protect your computer from hackers is important to you (and it should be!), my overall message is to be somewhat paranoid when your go online. However, I also recommend you maintain some balance by always considering the odds of something being off.
For example, if a freelance SEO writing client I’m working with sends me an email with an attachment that I’ve been waiting for and expecting, I would download it and open it (for an extra layer of protection, one could use an anti-virus program to scan the attachment before downloading it) since the odds are high that it contains exactly what I expect it to. But if a client sends me an unexpected email with an attachment, I’d email them and double check if it was indeed them that sent it (this is to make sure their email wasn’t hacked and programmed to send virus-laden attachments to all of their contacts).
The more of the above techniques you use, the less likely you are to end up with your smartphone or computer becoming infected with something nasty, and the less likely you are to find yourself falling prey to identity theft via your online activities.
Now that you’ve read over these internet safety tips, you know why internet safety is important, you understand how to prevent computer viruses, you know why you should get the best computer virus protection you can afford, and you know how to minimize your risk of online identity theft. So which of these techniques do you use already? Which ones are you going to start using? Do you have any tips on how to protect your computer that you’d add to this list? Comment below.
Know anyone who would benefit from this information? Please share it with them!

Thank you so much for this article, Avery. It’s very informative and very important to know these things.
I’m so glad you found it helpful! 🙂
Thanks again for all the great tips!
My pleasure Barbara! 🙂